[ad_1]

Cisco Safety analyzed Snort telemetry coming from Cisco Safe Firewalls to determine probably the most incessantly encountered guidelines by the lens of the MITRE ATT&CK framework.
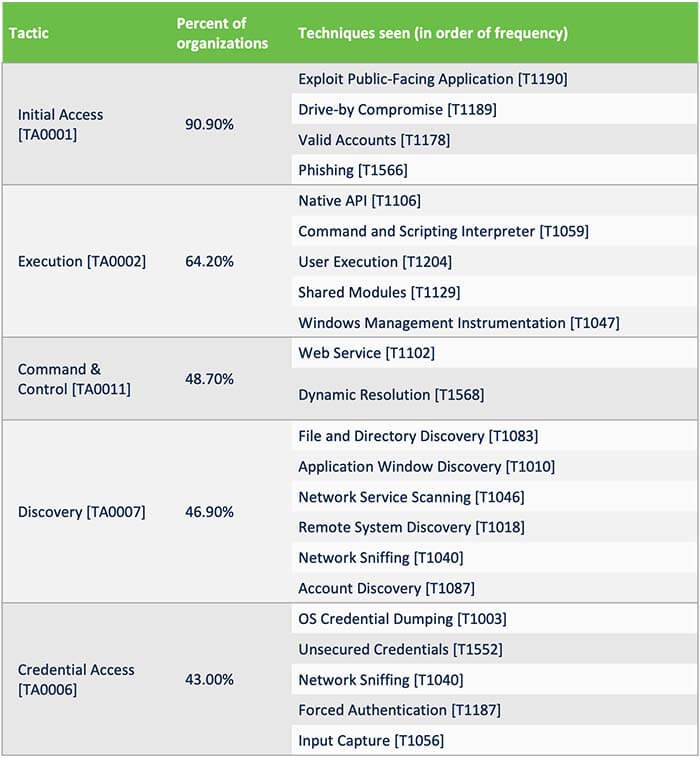
The MITRE ATT&CK framework describes attacker conduct as ways and consists of the actions attackers take to perform that conduct as strategies. Many frequent firewall guidelines will be mapped to MITRE ATT&CK; the above chart lists the ways and related strategies firewalls incessantly encounter.
By far, a firewall is extra more likely to see extra Preliminary Entry makes an attempt, which is sensible given its place on the community perimeter. Because the above chart exhibits, 90.9% of organizations noticed firewall alerts that fell underneath this tactic. Inside this group, organizations noticed exploit makes an attempt in opposition to public-facing functions, equivalent to Apache Struts, Bash, and Alternate Servers. One other incessantly detected method related to Preliminary Entry was the Drive-by Compromise method, which incorporates makes an attempt to hook up with spoofed web sites and entry to SMB shares.
Execution makes an attempt had been the second most frequent on this listing, detected by 64.2% of organizations. Widespread guidelines that triggered the sort of alert included vulnerabilities in content material administration methods (CMS), the Zeroshell Linux vulnerability, and an Apache Struts code execution vulnerability.
Apache Struts additionally featured prominently underneath Privilege Escalation and Defensive Evasion, two MITRE ATT&CK ways that did not make the highest 5.
Command and Management exercise was the third most incessantly encountered tactic, with 48.7% of organizations that noticed visitors of this sort. A lot of this visitors consists of suspicious DNS queries, which level to recognized or probably command-and-control methods.
The Discovery tactic consists of strategies equivalent to making an attempt to traverse administration information in a CMS in addition to DNS BIND info disclosure makes an attempt. The Discovery tactic was fourth most incessantly detected.
The Credential Entry tactic rounds out the highest 5. Methods embody credential dumping assaults, equivalent to these focusing on routers and IoT gadgets equivalent to CCTV cameras. Organizations additionally noticed firewall alerts for makes an attempt to use vulnerabilities that might present administrator credentials or makes an attempt to entry PHP configuration information.
Learn extra about firewall risk traits on the Cisco Safe weblog.
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.