[ad_1]
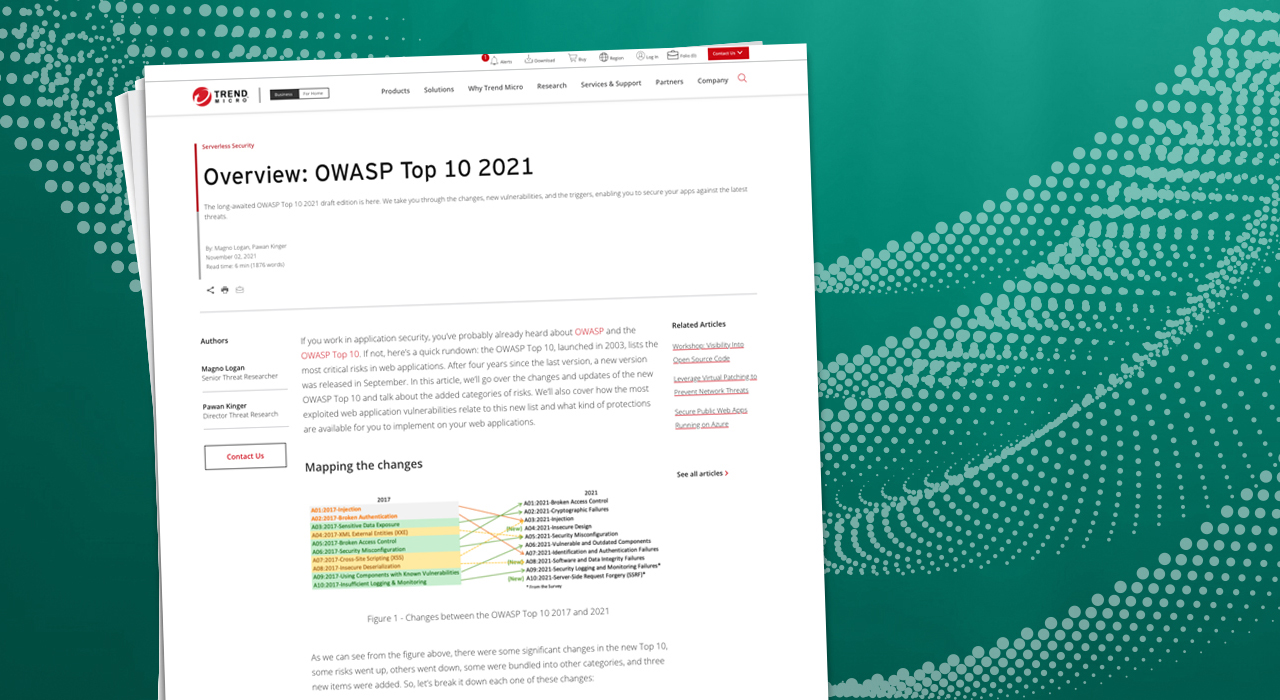
Desk 1 – The highest 15 vulnerabilities with identified exploits or proofs of idea and associated High 10 dangers
Easy methods to safe code by way of utility safety and testing
Now, let’s concentrate on tips on how to safe your apps from these vulnerabilities. This may be tough given you’ll be able to have tens, lots of, or perhaps hundreds of builders writing and deploying code day by day in your manufacturing surroundings.
First, organizations should make sure that all communications are being made utilizing TLS encryption. This needs to be utilized even amongst inside companies like load balancers, utility servers, and databases.
Organizations can considerably cut back the assault floor of their programs simply by limiting and monitoring uncovered companies, ports, and API endpoints. Right here, it’s important to consider container base photos and the programs on which its clusters are operating.
There are numerous code safety verifications so as to add to your pipeline to make sure that one’s code is secured:
Static utility safety evaluation (SAST) – That is additionally known as “safety code assessment” or “code auditing” and continues to be the most effective and quickest methods to detect safety points in a single’s code. Enterprises ought to have at the least one static evaluation instrument embedded into the pipeline whatever the language getting used. This instrument will examine for unsafe coding practices each time builders commit new code into the applying. As well as, the OWASP Basis has a listing of open-source and industrial instruments designed to research supply code or compiled code to detect safety flaws.
Dynamic utility safety evaluation (DAST) – Though dynamic evaluation can solely be carried out when there’s a operating utility to check towards, it’s also a good suggestion to carry out automated scans and checks to check for widespread utility assaults corresponding to SQL injection, XSS assaults, and cross-site request forgery (CSRF) assaults. These instruments may also check your utility, container, and cluster resilience when confronted with a collection of surprising load and malformed requests. As well as, OWASP has a dynamic evaluation instrument that can be automated and embedded into the pipeline known as OWASP Zed Assault Proxy (ZAP).
Software program composition evaluation (SCA) – Between 70% and 90% of all cloud-native purposes are fabricated from libraries or third-party dependencies. These codes are typically not checked in the course of the static evaluation part. Nevertheless, instruments just like the OWASP Dependency-Verify can be utilized to examine for outdated or susceptible libraries in a single’s code. Development Micro Cloud One™ – Open Supply Safety by Snyk supplies cloud-native utility safety by way of steady monitoring and figuring out open-source code vulnerabilities and license dangers in utility parts.
Runtime Software Self-Safety (RASP) – RASP is a strong utility safety instrument that kicks in when an utility begins, offering real-time or speedy safety towards threats and assaults, corresponding to zero-day exploits, XSS assaults, and e-mail and messaging app assaults. RASP not solely detects assaults but in addition analyzes the assaults’ habits and the context of the habits. Because of this it could possibly accurately pinpoint professional requests from assaults, minimizing false positives and grey alerts. Development Micro Cloud OneTM – Software Safety affords RASP, permitting builders to design and deploy safe purposes and defend towards subtle assaults shortly and effectively.
Patching and making certain that correct configurations are set are separate monitoring objects. The accountability for these rests with the applying house owners and their utility safety groups. DAST and penetration testing are normally useful in figuring out vulnerabilities and configuration points. As well as, enterprises can deploy programs that may stop such from occurring or carry out digital patching, corresponding to an internet utility firewall (WAF) or an IPS.
Conclusion
Securing your fashionable apps towards right this moment’s most harmful vulnerabilities doesn’t should be sophisticated, however it does require some care. Be taught extra about how a platform strategy can automate and streamline safety from construct time to runtime by testing the strong Development Micro Cloud One documentation website. In case you’re able to attempt it for your self, get began with a free, 30-day trial.
[ad_2]
