[ad_1]

Organizations working to cut back publicity to assaults concentrating on the Log4j distant code execution (RCE) vulnerability disclosed Dec. 9 have a few new issues to bear in mind.
Safety researchers at Blumira have found that risk actors can probably set off the RCE flaw on inner and regionally uncovered Log4j purposes through a JavaScript WebSocket connection — suggesting the assault floor could also be a lot bigger than first thought. In the meantime, the Apache Basis over the weekend launched one more replace to repair a 3rd vulnerability within the logging framework in latest days, that means that organizations will as soon as once more must patch their software program to stay absolutely protected towards the risk.
In accordance to Blumira, attackers can exploit the Log4j RCE flaw by luring customers to any server that runs JavaScript to provoke a WebSocket connection. WebSocket is a communication protocol that many trendy browsers use for bidirectional communication between the server and shopper. The location would make calls to the consumer’s system or native community utilizing WebSocket. If the sufferer’s host is susceptible, it’s then pressured to name out to a different attacker-controlled web site over LDAP, RMI, DNS, HTTP or different protocol and obtain malicious JavaScript for exploiting the Log4j RCE, says Matthew Warner, CTO and co-founder of Blumira.
“If the sufferer had a susceptible model of Log4j and it was logging out requests to paths being requested and/or the origin of these requests, it might set off the Log4j JNDI lookup to the malicious host,” Warner says. “No extra effort can be required.”
Warner says Blumira’s analysis exhibits the influence of Log4j is not restricted to susceptible servers.
“Anybody with a service that makes use of a susceptible Log4j model on their machine or native personal community can browse a web site and probably set off the vulnerability,” Warner says. It considerably expands the assault floor and is one other weapon that operators of phishing and malicious promoting scams are prone to exploit, he says.
The brand new assault vector shouldn’t complicate issues for organizations that already are following the really helpful remediation steps for Log4j. “Nevertheless, it does spotlight the significance of patching all native improvement and inner servers,” Warner says.
Three Vulnerabilities — So FarLog4j is a near-ubiquitous logging device in Java environments. Since Dec. 9, three distinctive vulnerabilities have been disclosed within the logging framework, every of various severity. Probably the most severe one is the vital RCE vulnerability (CVE-2021-44228) that the Apache Basis disclosed Dec. 9.. The flaw exists in a Java Naming and Listing Interface (JNDI) lookups characteristic that’s enabled by default in variations Log4j 2.0-beta9 to Log4j 2.14.1.
Attackers can exploit the characteristic to take full distant management of susceptible techniques, which might embody Web-facing techniques, inner techniques, community parts, digital machines, industrial management and SCADA techniques, and cloud-hosted belongings.
The Apache Basis launched an up to date model of the logging framework (Log4j 2.15.0) for Java 8 customers on Dec. 10 to deal with the vulnerability amid experiences of attackers actively searching for to take advantage of the flaw.
It then adopted up with a second replace on Dec. 13 (Log4j 2.16.0 for Java 8 and Log4j 2.12.2 for Java 7) as a result of the unique repair mainly ended up opening techniques to denial-of-service (DoS) assaults (CVE 2021-45046) below sure situations.
On Dec. 18, the Apache Basis issued one other replace (Log4j 2.17.0 for Java 8) to deal with a 3rd, infinite recursive vulnerability in Log4j (CVE-2021-45105) that it described as permitting for DoS assaults.
“Infinite recursion is code calling itself time and again and once more,” says Saryu Nayyar, CEO of Gurucul. “Finally, it should overflow the reminiscence allotted to it, and supply the power to inject malicious code outdoors of the outlined reminiscence area.”
Each CVE 2021-45046 and CVE-2021-45105 can solely be exploited below particular nondefault situations and are subsequently thought-about much less extreme than CVE-2021-44228, the flaw that was disclosed on Dec. 9, which impacts a really vast swath of organizations.
In accordance with safety researchers at Google, the bug impacts greater than 35,000 Java packages — or greater than 8% — of all packages on Maven Central, one of many largest repositories of Java packages. The pervasiveness of the flaw and the relative ease with which it may be exploited has attracted widespread consideration throughout the risk actor neighborhood.
Safety distributors have reported seeing quite a few financially motivated attackers in addition to state-backed risk teams from nations equivalent to Iran, China, and Turkey actively attempting to take advantage of the flaw.
The exercise prompted the US Cybersecurity & Infrastructure Safety Company (CISA) to problem an emergency directive Friday ordering all civilian federal companies to take a collection of measures to determine, patch, or mitigate susceptible techniques. Businesses have till Dec. 23 to adjust to the necessities of the directive.
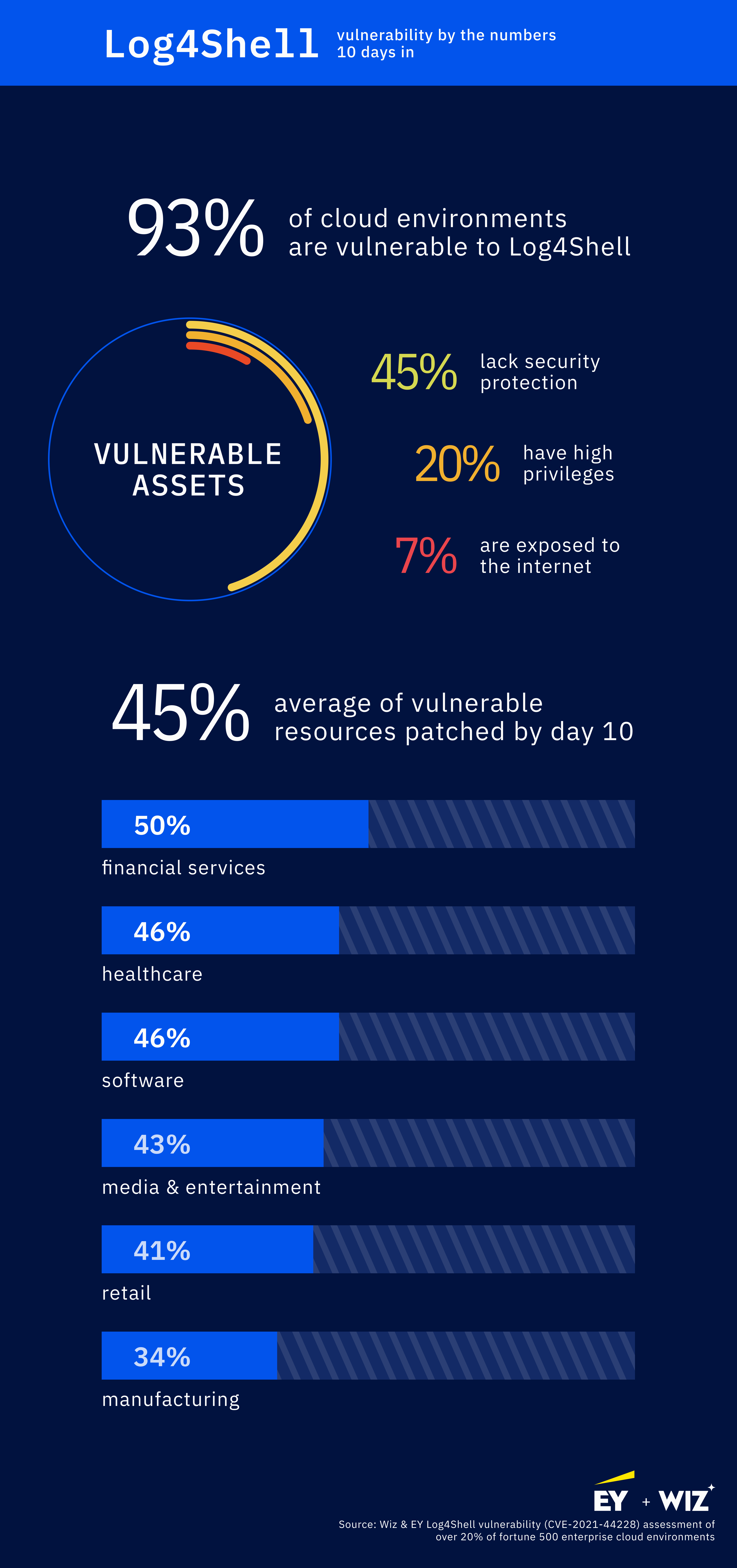
The newest developments come amid indicators that organizations are making at the very least some progress in addressing the risk. An evaluation that cloud safety vendor Wiz carried out exhibits that 10 days after the flaw was disclosed, organizations on common have patched some 45% of their susceptible cloud sources. Nevertheless, the seller discovered that 45% of susceptible machines stay unprotected towards the risk. Of those techniques, 25% had administrative privileges and seven% had been uncovered to the Web.
In the meantime, a dashboard
that Sonatype launched this week to trace Log4j downloads confirmed that there have been greater than 4.6 million downloads of the logging device since Dec. 10. Forty p.c of what the corporate described because the “most up-to-date downloads” had been of susceptible variations of Log4j.
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.