[ad_1]

The continued wrestle to replace weak software program by discovering and making use of the fitting patches in a well timed method has led half of enterprise IT departments to make use of Internet utility firewalls (WAFs) both in lieu of patching or to supply some safety earlier than patching may be achieved.
This comes from a brand new Darkish Studying report, “How Enterprises Are Securing the Utility Surroundings.” The survey requested 136 IT, cybersecurity, and utility growth professionals from organizations throughout greater than 20 trade verticals about their utility growth practices.
The issue of discovering and making use of safety patches is well-known. In a latest sequence of ransomware experiences, cyber-risk administration firm Black Kite famous that patch administration was a unbroken weak point throughout industries as assorted as prescribed drugs and auto manufacturing. Whereas secure and dependable automation is in growth, IT departments typically need to make do with risk-based administration and harm-reducing workarounds.
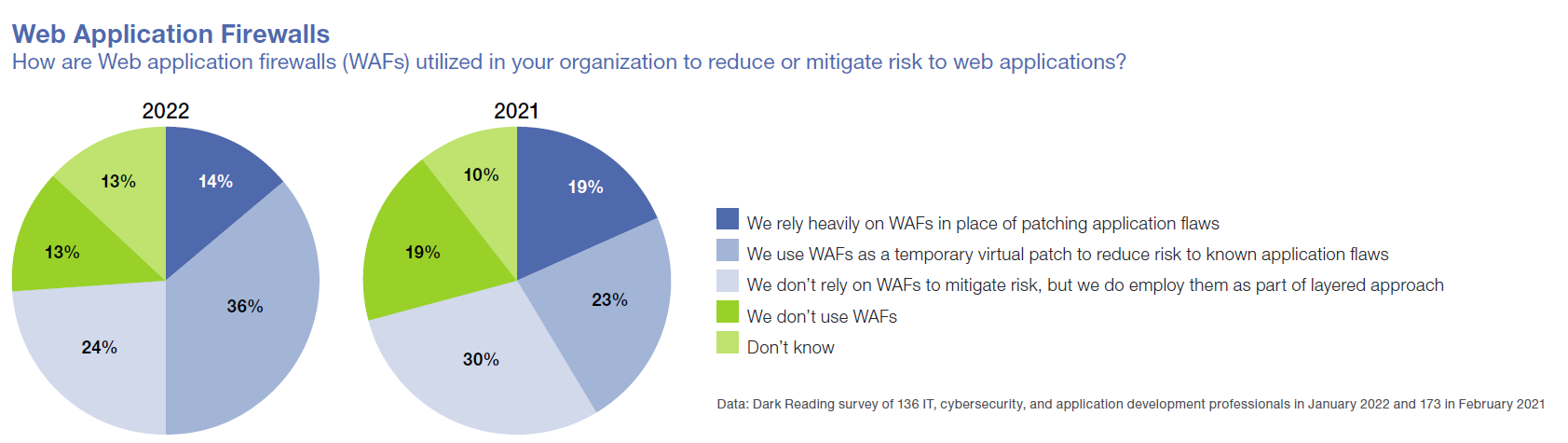
When the Darkish Studying survey requested respondents in 2022 how they use WAFs to cut back danger to their Internet functions, 14% admit to utilizing WAFs as a substitute of patching flaws, and 36% say they use WAFs as a brief safeguard earlier than getting round to patching. Nonetheless, that is an enchancment over 2021, when the numbers have been 19% and 23%.
How enterprises make use of WAFs shifted greater than the variety of corporations that use the instrument. The share of respondents who say they use WAFs as part of layered defenses relatively than as a type of short-term patch dropped from 30% in 2021 to 24% in 2022. Nevertheless, the entire p.c of those that use WAFs stayed practically the identical — 74% in 2022 versus 72% in 2021. It appears that evidently regardless of the know-how’s shortcomings, WAFs proceed to be helpful substances within the cybersecurity pantry.Sustain with the newest cybersecurity threats, newly-discovered vulnerabilities, information breach data, and rising developments. Delivered every day or weekly proper to your e-mail inbox.Subscribe
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.