[ad_1]

Automated scanning, improved assault instruments, and new methods to monetize compromises have turned cloud workloads and server cases into prime assault targets, Google Cloud said in its inaugural “Risk Horizons” report, revealed Nov. 23.
These vectors aren’t new, however they show constantly efficient amongst attackers. Google Cloud’s report discovered intruders targeted on misconfigurations, poor buyer safety practices, and weak third-party software program to compromise practically 75% of cases. The information comes from its evaluation of fifty lately compromised Google Cloud Platform (GCP) cases, wherein 48% had weak — or no — passwords, 26% had a vulnerability in third-party software program, and 12% had been compromised by way of misconfiguration.
All of those threats are properly understood however stay efficient methods to compromise programs resulting from human error, Bob Mechler, director within the workplace of the CISO at Google Cloud, wrote in a weblog put up.
“Whereas cloud prospects proceed to face a wide range of threats throughout purposes and infrastructure, many profitable assaults are resulting from poor hygiene and a scarcity of fundamental management implementation,” he wrote, together with Google Cloud’s safety editor, Seth Rosenblatt. “Given these particular observations and common threats, organizations that put emphasis on safe implementation, monitoring and ongoing assurance can be extra profitable in mitigating these threats or on the very least scale back their general affect.”
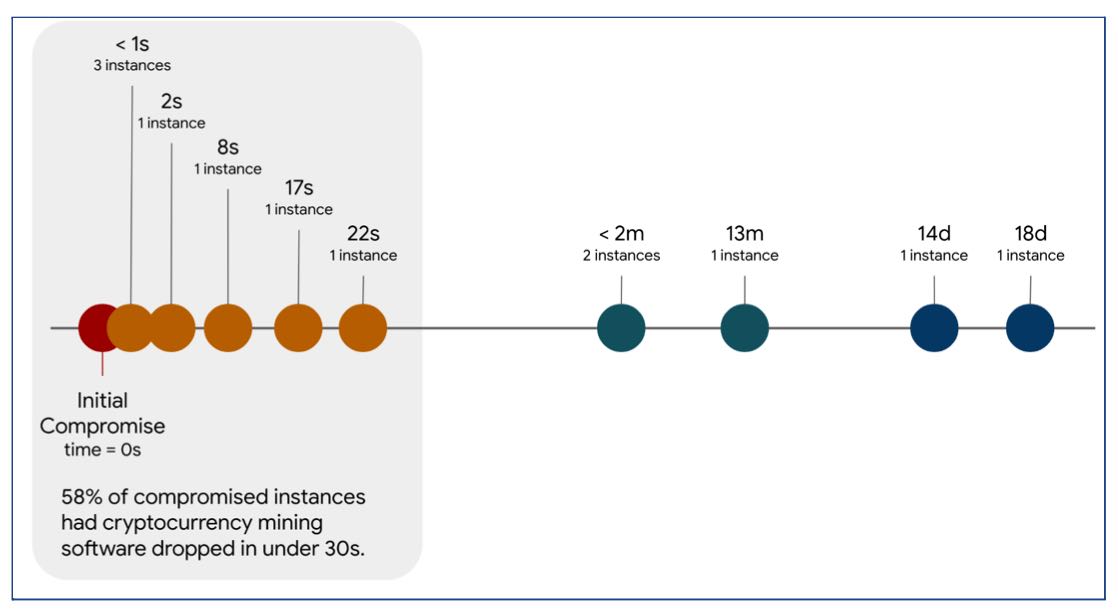
The mix of misconfigured cloud cases and automatic assaults meant the house owners of cloud workloads had little time to shore up defenses. In 40% of cases, the compromise occurred in lower than eight hours; in a minimum of one case, in as little as half-hour.
Attackers generally monetize compromises utilizing cryptocurrency mining software program or ransomware, and sometimes try to assemble credentials by way of phishing assaults to increase their management over compromised computer systems and companies. The commonest manner for attackers to make the most of a compromised occasion on Google Cloud Platform (GCP) was to put in cryptocurrency mining software program, which occurred in 86% of cases following a compromise.
The payload supply additionally occurred very quick — greater than half of compromised cases had cryptomining software program delivered in below 30 seconds, in accordance with the report.
“This implies that the preliminary assaults and subsequent downloads had been scripted occasions not requiring human intervention,” Google Cloud said within the report. “The flexibility to manually intervene in these conditions to forestall exploitation is almost inconceivable. The perfect protection can be to not deploy a weak system or have automated response mechanisms.”
In one other 10% of instances, the attackers used the compromised occasion to scan the Web for different weak targets, the corporate said in its report.
The report brings collectively knowledge and insights from a number of inner Google groups, together with the Google Risk Evaluation Group (TAG), Google Cloud Safety and Belief Middle, and Google Cloud Risk Intelligence for Chronicle, Belief and Security.
These menace intelligence and safety teams additionally found an operation launched by the Russian government-backed Fancy Bear group, also referred to as APT28, which used greater than 12,000 Gmail accounts in a phishing marketing campaign that tried to assemble Google account credentials from focused customers. As a result of the group used a significant supplier, the phishing messages handed the anti-spam safety examine, Sender Coverage Framework (SPF)
The assaults most closely focused the US, United Kingdom, and India, but additionally focused different nations, together with Brazil, Canada, many European Union nations, and Russia.
Google really helpful corporations concentrate on guaranteeing that deployed software program and workloads are configured with robust safety. Along with commonsense safety measures, similar to two-factor authentication and common automated scanning of the Internet software, corporations must have instruments in place to forestall the unintended publicity of passwords, keys, and certificates when publishing code. Any third-party code utilized in an software must be vetted and be hashed as an integrity examine. And firms ought to acknowledge that the advantages of the cloud include some caveats, the report said.
“Regardless of the rising public consideration to cybersecurity, spear-phishing and social engineering ways are regularly profitable,” Google said within the report. “As for different types of IT safety, defensive measures have to be strong and layered to guard cloud sources resulting from ubiquitous entry.”
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.