[ad_1]
Methods to Safe and Combine Your Azure DevOps CI/CD Pipeline
Serverless Safety
Discover experiments from Chuck Losh, Resolution Architect, to discover how Utility Safety can assist defend your functions at runtime as they’re constructed, and combine together with your automated Azure DevOps CI/CD pipeline with automated testing.
By: Chuck Losh
August 13, 2020
Learn time: ( phrases)
Okay, let me begin off by saying this was quite a lot of enjoyable to experiment, be taught, and check! I needed to share this private expertise with you! Azure DevOps is a superb toolset! It is extremely intuitive and straightforward to make use of! Pattern Micro gives nice runtime utility safety for container-based workloads with Pattern Micro Cloud One Utility Safety. So, how can we combine these two nice applied sciences collectively, and be sure that runtime container safety is enabled? Nicely, I’m going to point out you right now with some studying experiments that I arrange!
First, we’re going to check every little thing domestically in our IDE with Microsoft Visible Studio Code. As soon as we’re happy with these assessments, we’ll push the code as much as Azure DevOps and make some construct and launch pipelines. These pipelines will construct our app right into a container and host it inside an Azure App Service Plan/Azure Internet App. Then, we’ll add Pattern Micro Utility Safety to guard our utility at runtime contained in the container picture. We may also experiment with the brand new Azure Container Construction Checks (Preview) in our Azure DevOps construct pipeline. This will likely be used to run some assessments that I constructed to make sure that the Pattern Micro Cloud One Utility Safety library is included in our container picture construct.
Okay, let’s get began! I’m going to make use of a check a Django hello-world Python utility.
django admin begin undertaking helloworld
That is proven beneath. The place the app surroundings is setup in Visible Studio Code, and the DockerFile was generated for the undertaking by utilizing the Add DockerFiles possibility with the Visible Studio Command Palette.
When you do this, the auto-generated DockerFile and Python undertaking ought to be fairly much like what I’ve beneath.
Okay, let’s go forward and make the most of essentially the most glorious Docker extension for Visible Studio Code. Extensions in Visible Studio Code are fairly cool! Observe: that is below the idea that you’ve got Docker CE/Desktop for Home windows already working in your desktop. In the event you do not I might suggest working the next choco command to put in Docker through Chocolately.
choco set up docker-desktop
The three (Visible Studio Code, Docker, Docker Visible Studio Code extension) work in tandem collectively! You’ll be able to right-click your DockerFile and select the construct possibility with the extension. It will will let you construct a container picture of the check undertaking domestically.
Right here, you’ll be able to see on the left, my check container is being constructed and added to my native machine container registry. On the fitting you’ll be able to see the DockerFile being executed. Bonus alert! You’ll be able to you’ll be able to add/combine your Azure Container Registry which I’ve executed. This extension is certainly, fairly cool! As soon as your container has completed constructing, you’ll be able to run your container by choosing the picture that was simply constructed and right-clicking. You must select the choice to run the container interactive. I like to decide on interactive, that means I can see the run log data within the in-built terminal. You also needs to see the working container within the higher left you’ll be able to all the time right-click and cease at anytime.
Okay, cool, from the output now we have a working check container on our native system. Let’s have a look at if we are able to get to the Django Python helloworld check undertaking in a browser. From the terminal output we are able to see that it’s working on the localhost on port 8000.
Wonderful! So, now that now we have this check Django python utility working domestically. Let’s go forward and publish this code to a personal Azure DevOps Repo in a brand new undertaking.
I went forward and logged into my Azure DevOps subscription, and created a brand new personal undertaking known as Take a look at App Sec. I then created a brand new Repo and cloned it to my native system by utilizing the Clone in VS Code possibility. This course of is illustrated beneath!
Okay, now I dedicated my check undertaking to Azure DevOps utilizing the in-built supply management instruments constructed into Visible Studio Code. That is proven beneath.
Cool, now I’ve my check supply code checked in efficiently to Azure DevOps!
Nicely, earlier than we check out and add Pattern Micro Utility Safety, let’s simply go forward and construct an related Azure DevOps Construct Pipeline and Launch Pipeline to Azure Internet App. Sound good? Okay, sounds good to me! Let’s go!
Okay, on this instance pipeline. I’m going to take you thru the wizard for the setup. On the primary Pipelines display you’re going to need to hook it as much as our present Azure Repo. So, we choose the Azure Repos possibility.
Okay, subsequent, let’s choose our Repo that we created and dedicated the code modifications from Visible Studio Code.
Okay, so what we’re going to do is construct and push a picture to Azure Container Registry. Let’s select that Docker possibility!
When you choose that possibility, it’ll need to logon to your out there Azure subscriptions. Select the subscription you need to use that comprises an lively, or new Azure Container Registry. Select your related Azure Container Registry that you just need to use, and put within the acceptable picture title. The DockerFile ought to robotically pull out of your supply Repo as proven.
Then, click on validate and configure. What is going to occur is it would robotically create a pipeline.yaml in your Repo to your assessment. You’ll be able to select to avoid wasting this, or go forward and save and run. We’ll go forward and select save and run, and see if the check picture will get constructed and pushed to our Azure Container Registry.
Okay, we are able to see that the construct has kicked off, and now we have our standing data for the CI construct pipeline.
Okay, after a couple of minutes, it appears to be like like now we have a profitable container construct!
Okay, lets take a peak at our Azure Container Registry, and ensure the picture arrived on the opposite aspect. Yep, appears to be like prefer it created the Repo and the pictures on the opposite aspect. So, we’re good there! Clearly, I’ve executed a bunch of check builds, so my tags have gone up! Manner up! I received carried away there!
Okay, the subsequent step is to construct a launch pipeline to tug the related container picture from Azure Container Registry, and serve it up inside Azure Internet App/App Service Plan. Let’s go!!
Right here is my accomplished launch pipeline. You’ll be able to create one within the releases part of Azure DevOps. It will full the CI/CD cycle.
To begin this, we need to begin with the artifacts part proven above earlier than our deployment levels. We’re going to set off an automatic / triggered deployment based mostly on a profitable container picture construct of our utility.
Let’s break that down!
Launch (deployment) templates are going to be your buddy, they usually robotically come up whenever you begin a brand new launch pipeline. Proven beneath for instance.
We’re going to choose the Azure App Service deployment template. Since we’re going to deploy our constructed container picture to Azure App Service.
That can set the stage, so to talk! Okay, unhealthy joke! However, sure, we are able to see that the stage has already been added to the pipeline, and our clean artifacts sections is able to be configured.
Let’s click on on including an artifact, so we are able to choose that based mostly on a profitable construct from our container construct pipeline.
Cool! Subsequent, we’re going to hit the lighting bolt icon on the construct artifact and configure the continual deployment set off.
It will current your triggered occasions wizard. We’ll allow it with the slider for steady deployment based mostly on each time a brand new container construct is out there and set it to our grasp department with the filtering possibility.
This manner we do not have to fret about setting a schedule. Let’s go over to the levels part and click on the lightning bolt to take a look at the pre-deployment situations/triggers. We need to be certain that the after launch possibility is checked, and the construct/ref artifact is chosen. It will be certain that the automation is in place as a substitute of guide. You too can do some cool issues in there like add approvers and gates.
Approvers instance is proven beneath, and you will get a pleasant e-mail notification from Azure DevOps notifying you have got the pending approval request, and the commits/construct data will likely be displayed for assessment. Great way so as to add a human gate test!
Wow! That is actually cool! Okay, keep on activity! Talking of duties, that is what we’re going to configure subsequent on the stage. As soon as we click on “1 activity/job” on the stage, we are able to configure the deployment to Azure App Service.
That is the place you’re going to choose your Azure Subscription, App kind, and App Service Plan. On this case, I chosen the Internet App for Containers, and my related Azure Container Registry the place my construct picture will reside to tug from.
Okay, that is it! Our automated launch pipeline is finished, and depending on a profitable construct pipeline. I made a decision to take out the approvers possibility and simply let it circulation via for testing.
Let’s go forward and set off a check launch deployment to ensure that launch pipeline works!
Okay, appears to be like like that labored so far as the discharge pipeline. Let’s test to see if our container based mostly net utility is out in Azure Internet App.
Yep it’s! We will go to the positioning in Azure.
We will even see on the Azure App Service aspect within the Deployment Heart our profitable deployments log, and the container settings that its pulling the correct construct/picture from Azure Container Registry. Appears like every little thing is speaking and dealing!
Okay, now now we have our construct and launch pipelines working! I feel it is time that we’re going to deploy Pattern Micro Cloud One Utility Safety! It will present an extra layer of runtime safety for the container based mostly utility.
First, in our supply code domestically, we’re going to add the modifications via our Visible Studio Code integration. We’ll check domestically to ensure Pattern Micro Cloud One Utility Safety is working!
After a profitable native check, we’ll difficulty a Visible Studio Code commit/push to Azure DevOps. This could robotically set off a profitable CI/CD construct/launch pipeline.
To try this for Python, we want do a few issues so as to add it (Pattern Micro Cloud One Utility Safety) to the container picture.
First, we might want to add the Pattern Micro Cloud One Utility Safety safety library to our necessities.txt. That’s proven right here.
Subsequent, we have to add one line to wsgi.py to import/use the put in safety library. That’s proven right here.
import trend_app_protect.begin
Lastly, we might want to invoke some startup surroundings variables, in order that when the app/container begins up it would name dwelling and register to your Pattern Micro Cloud One Utility Safety console. These will be generated proper in your Pattern Micro Cloud One Utility Safety console by creating a brand new group. The console is proven right here beneath for illustrative functions. By hitting Create New Group, you’ll receive the important thing and secret values to plug in as required surroundings variables. You’ll be able to see my group is SA PYTHON TEST.
Okay, lets see if this all works domestically!
Okay, properly the container is working domestically! I checked the Pattern Micro Cloud One Utility Safety Console, and I get a inexperienced gentle that the appliance agent is now related to the console below the Python group I created. I may ssh the container domestically with the Docker exec command, and I see that the trend_app_protect.log file says that the agent is related and agent is prepared! Huzzah!
Okay, so let’s run a fast check with a check malicous curl script to check whether or not the safety is enabled.
curl -H “Person-Agent: () { :; }; /bin/eject” http://127.0.0.1:8080
Huh, that is unusual it returned outcomes! That should not occur. Oh!! I have to activate the respective safety module within the coverage. Foolish me! My mistake! My fault!
Okay, now I’ve all of the safety modules turned on for that Python utility group so as to present real-time safety to the appliance that registers to this group.
Alrighty then, let’s run that native check once more! Lets?
Okay, that point the block labored as anticipated! The return worth was 403/blocked. Let’s try the console.
Huzzah! The try reveals blocked! I’ve the date/time stamp data, and the inexperienced app connection standing gentle has now turned to pink!
On the main points of the malicious payload occasion, we are able to see that it was blocked in real-time! Even the information of the check malicious payload that I executed is proven. Fairly cool!
Okay, so appears to be like like all native assessments are working as supposed, and our check utility nonetheless hundreds usually in our native browser!
Let’s go forward and do a commit of our modifications, and kick off a brand new Azure DevOps CI/CD construct. That means we are able to introduce Pattern Micro Cloud One Utility Safety to our pipelines, and check manufacturing utility in Azure Internet App.
Okay, so these surroundings variables to your Pattern Micro Cloud One Utility Safety! We’re going to ensure that they exist inside our Azure App Service plan. That means when the container is launched, it would name in these values to the Utility Safety Agent.
You too can set them in your launch pipeline in Azure DevOps if you want. That’s what I did. You are able to do that right here. That means when the discharge is triggered you can be positive they’re saved within the related Azure App Service plan as surroundings variables above.
So, I ran a commit and push inside Visible Studio Code, and this robotically kicked off a brand new construct pipeline. How thrilling!
You’ll be able to see the automated construct based mostly on commit/push!
The construct was profitable! Which in flip, the construct robotically kicked off a brand new CD launch/deployment pipeline.
Cool! Our up to date launch was profitable with utility safety, and efficiently deployed to Azure!
Our utility now has been efficiently up to date with Pattern Micro Utility Safety Safety!
Let’s test the Pattern Micro Cloud One Utility Safety console and see if it has known as dwelling.
Eureka, it has! Cool! Now, now we have efficiently deployed our container based mostly utility to Azure Internet App inside an related Azure App Service Plan. We even have working construct and launch pipelines with Azure DevOps! Every part assessments and appears to be working with our studying experiments!
Okay, very last thing earlier than you go! I needed to see if I might run some automated assessments in Azure DevOps to ensure that Pattern Micro Cloud One Utility Safety is included in each construct, and that it’s not eliminated by chance or possibly on function.
I can accomplish that with…….drumroll……a Container Construction Take a look at (Preview)!
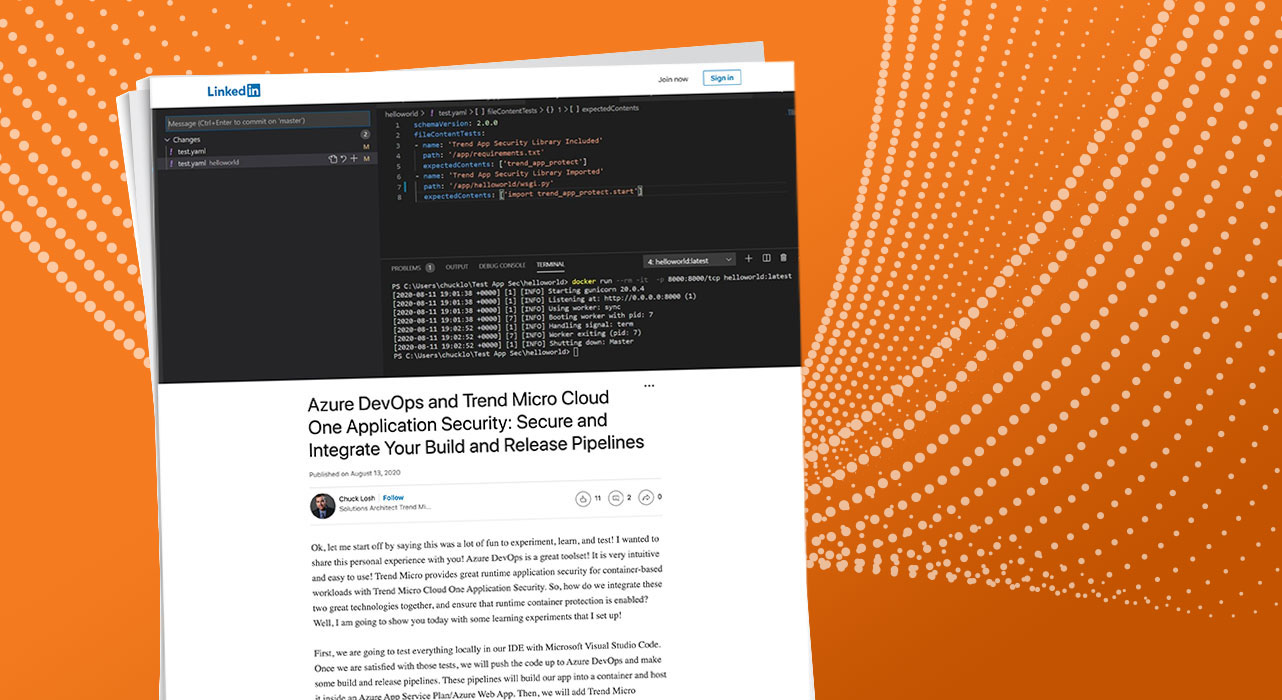
Right here is my setup with the Container Construction Take a look at Azure DevOps Process in my construct pipeline. The config file for the assessments is a Yaml file that I setup.
Within the Yaml config file, you’ll be able to see that I’m utilizing the file content material assessments. I’m testing that trend_app_protect is included in my necessities.txt file, and I’m checking my wsgi.py loader file to ensure that I’m importing the safety library.
Okay, cool, so now we have our Yaml config file that we’re going to use for analysis of the container picture.
Let’s go forward and commit that Taml file to supply Repo. As soon as we do this, one other automated CI/CD construct and deployment will kick off. Let’s ensure that works as supposed first earlier than truly making an attempt to take away Pattern Micro Cloud One Utility Safety. We must always have the ability to go into our construct pipeline, and see the assessments carried out and the outcomes of these assessments.
Okay, we are able to see the construct is full and the following launch. We will additionally see that now we have the assessments that have been carried out below Checks and Protection they usually have been 100% handed lets check out the main points of the assessments.
Listed below are the check particulars that have been carried out by the Yaml configuration file that was using the Container Construction Take a look at assemble.
Okay, very cool! Our Launch labored was profitable as a result of the construct pipeline assessments have been profitable. So, this model/deployment of the appliance is now working in Azure Internet App, and in addition as an added bonus presently protected by Pattern Micro Cloud One Utility Safety.
Let’s go forward and take out the inclusion of importing the safety library, and commit that to Azure DevOps and see what occurs! Primarily, what we’re doing is disabling Pattern Micro Cloud One Utility Safety.
Right here you’ll be able to see that I dedicated the elimination of the appliance safety library import.
Right here you’ll be able to see that the automated construct has failed as a result of my assessments are at the moment are at 50 % handed. So, there is no such thing as a subsequent linked launch pipeline. The software program in manufacturing continues to be on the earlier launch, and presently nonetheless protected by Pattern Micro Utility Safety. That’s what we would like. Let us take a look at the check particulars and see which check failed.
Okay, we see there that the Container Construction Take a look at failed on the File Content material Take a look at: Pattern App Safety Library Imported.
We can also visually affirm right here that no launch is related to the failed construct, so we saved this explicit deployment from going to manufacturing with no lively Pattern Micro Cloud One Utility Safety Safety!
As soon as we put the safety library import code again in and commit, we are able to robotically launch the construct to an new deployment. Let’s do this! I need to depart our check utility and CI/CD in a great place!
Okay, in monitoring our CI/CD Pipeline appears to be like like we had a profitable construct this time! Each assessments handed at one hundred pc! Additionally, now we have a brand new corresponding launch and our utility is exhibiting on-line, deployed, and related and guarded with Pattern Micro Cloud One Utility Safety! I additionally connected an e-mail pattern alert of the construct that succeeded.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
[ad_2]
