[ad_1]

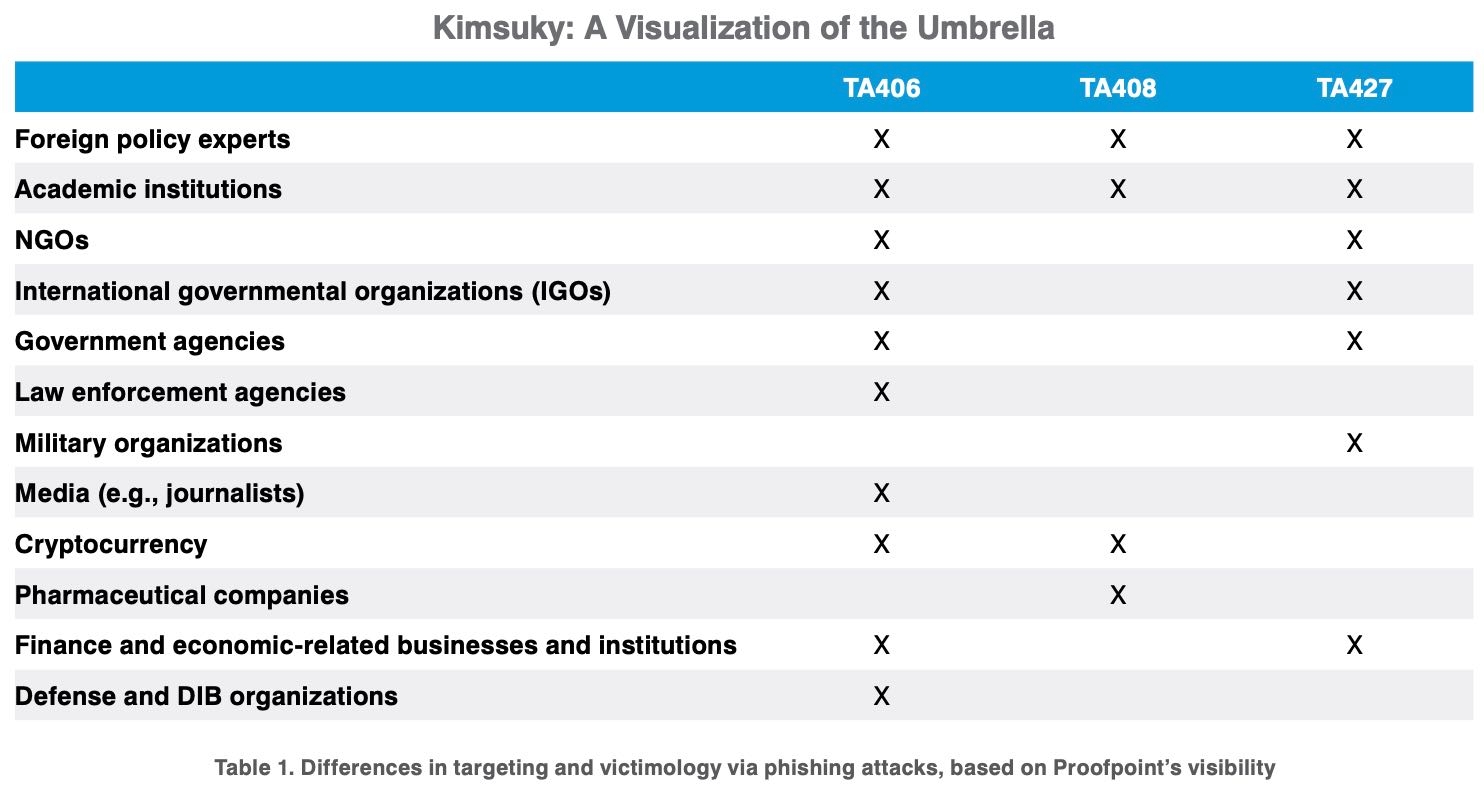
A North Korean cyber-operations group has elevated its concentrate on cyber espionage and concentrating on diplomats and regional specialists, utilizing captured person credentials to gas phishing assaults and solely not often utilizing malware to persist in focused organizations.A brand new report by message-security agency Proofpoint, which targeted on a single subgroup of what different safety companies name Kimsuky, discovered that the North Korean group primarily targets people in america, Russia, and China, and often makes an attempt to quietly harvest credentials, siphon off data, and — like many assaults attributed to North Korea — flip compromises into monetary achieve. The hacking group, which Proofpoint calls Menace Actor 406 (TA406), tried to compromise high-level officers, regulation enforcement leaders, and specialists in economics and finance in weekly assaults — a departure from lower-level assaults in previous years.As well as, previous to 2021, North Korean teams haven’t sometimes used nationwide safety points as a lure, however that has modified, says Sherrod DeGrippo, vice chairman of risk analysis and detection at Proofpoint.”Essentially the most notable elements of TA406 are their flexibility in utilizing any means for monetary achieve and their persistence in concentrating on the identical people [and] organizations repeatedly,” she says. “Like with different state-aligned teams, these aligned with North Korea range of their skillset and sure have ever-evolving targets primarily based on state pursuits.”Whereas cyber operations by China and Russia often garner essentially the most consideration, specialists have targeted just lately on actions by teams linked to Iran and North Korea. This week, the Cybersecurity and Infrastructure Safety Company (CISA) warned that assaults by Iran-linked teams are trying to take advantage of recognized vulnerabilities in Fortinet community home equipment and Microsoft’s Alternate server. North Korea’s well-known Lazarus Group has focused provide chains, compromising a South Korean security-software vendor and a Latvian IT asset-management vendor.Extra just lately, North Korean has targeted a lot of its efforts on espionage campaigns and concentrating on organizations for monetary achieve, with cryptocurrency a typical goal of assaults.”In early 2021, TA406 started virtually weekly campaigns that includes themes that included nuclear weapon security, U.S. President Joe Biden, Korean overseas coverage and different political themes,” the Proofpoint report acknowledged. “The group tried to gather credentials, reminiscent of Microsoft logins or different company credentials, from the focused people. In some instances, the emails have been benign in nature, [but] these messages could have been makes an attempt by the attackers to have interaction with victims earlier than sending them a malicious hyperlink or attachment.”Three North Korean GroupsThe report in contrast three subgroups of the sprawling North Korean cyber marketing campaign referred to as Kimsuky. The hassle included TA406, however Proofpoint additionally described how that group of operators differed from different subgroups, reminiscent of TA408 and TA427, which usually concentrate on a smaller subset of targets. The teams sometimes goal authorities, tutorial, media, and organizations linked to cryptocurrency.The teams have shifted extra towards quite a lot of strategies for harvesting credentials, particularly these usernames and passwords for political and monetary targets, the report acknowledged.”TA406 conducts credential-phishing campaigns that concentrate on specialists at political and overseas coverage organizations and NGOs, particularly those that are working with or are specialists on actions that affect the Korean Peninsula, together with nuclear nonproliferation,” Proofpoint acknowledged.Harvesting CredentialsThe attackers use quite a lot of totally different messaging platforms, together with working their very own programs primarily based on PHP servers, reminiscent of PHPMailer and Star, but in addition utilizing main service suppliers, reminiscent of GMail or Yandex, together with stolen or artificial identities to idiot focused people. In some instances, the cyber operations workforce additionally used malware to realize persistence in a selected atmosphere.”Credential harvesting campaigns sometimes focused a number of organizations at a time whereas malware campaigns have been deployed in restricted, very focused instances,” DeGrippo says. “In 2021, malware campaigns represented lower than 10% of total exercise attributable to TA406.”Attackers have more and more targeted on credential harvesting as extra staff make money working from home and entry cloud companies and on-line infrastructure, usually utilizing solely a username and password. Credential spraying, the place attackers try to make use of stolen or frequent passwords to realize entry to accounts, have skyrocketed previously yr, with greater than 193 billion tried logins in 2020, in keeping with Akamai.With cloud entry changing into more and more essential, the development has continued in 2021, with entry to distant desktop protocol (RDP) servers and digital personal community (VPN) home equipment among the many most useful credentials bought on-line, in keeping with IBM.
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.