[ad_1]
PCI DSS in motion
The primary breach that will come to thoughts is the Capital One hack that uncovered 106 million bank card purposes and led to a $80 million high-quality from US regulators. Let’s check out another breaches and the way they may’ve been averted by referencing the PCI DSS guidelines and objectives.
Passion Foyer
In early 2021, Passion Foyer was hacked. An impartial researcher that makes use of the deal with Boogeyman recognized the breach. He found a publicly accessible database on Amazon Net Providers (AWS) that contained delicate data from over 300,000 Passion Foyer prospects. The database was 138GB in dimension and had buyer names, addresses, cellphone numbers, and partial card particulars. Oddly in the identical database was the supply code for the corporate’s app, which is one other challenge altogether.
The breach was the results of a misconfigured cloud database that was publicly accessible. It is a clear violation of PCI DSS guidelines #3, #7, and #9, as a result of the cost card knowledge was being saved on an open server. Passion Foyer additionally did not adjust to rule #10, which states that entry to cardholder knowledge and related community assets should be tracked and monitored. This clearly wasn’t occurring, in any other case the misconfiguration would have been remediated and your entire ordeal finally averted.
Macy’s
The foremost retailer suffered a breach in October 2019, which uncovered the cost card numbers, safety codes, and expiration dates of consumers who used the web take a look at system with the My Account pockets web page. Whereas Macy’s didn’t reveal the variety of prospects impacted, the retailer clocked 55.7 million month-to-month on-line visits by April of that 12 months. And to be frank, stealing the knowledge of only one buyer is sufficient of a priority.
The breach occurred resulting from a focused Magecart assault that injected malware into the checkout and pockets pages. Macy’s was evidently in breach of a slew of PCI DSS guidelines, and what’s extra regarding is the truth that Magecart is well-known. In reality, Macy’s was simply one in every of many victims that 12 months, together with FILA, Ticketmaster, British Airways, and others. Earlier assaults on different main retailers ought to’ve motivated Macy’s to run safety audits and remediate any vulnerabilities as required by PCI DSS.
Why this issues to you
Everybody within the group performs an element in sustaining compliance. It begins on the prime with the CISOs after which trickles all the way down to SecOps and DevOps groups. In a perfect DevSecOps world, there isn’t any hierarchy in safety accountability between each groups—they work in live performance with one another. SecOps should assist DevOps groups perceive what they should do to, and builders should execute this on the software stage.
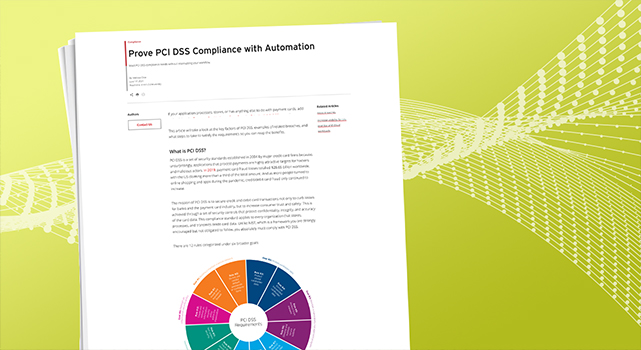
Following the 12 PCI DSS necessities, right here’s a number of examples of how steady compliance is a crew effort:
Rule #6: Builders should construct methods with safety in thoughts
Rule #8: Identification and entry administration should assign each consumer a novel consumer id-requirement eight
Rule #9: The bodily safety division should make sure that entry to the constructing and server rooms is managed
Rule #10: Safety operations should make sure that logs are created to file and observe entry to cardholder knowledge
Rule #11: Operations and improvement groups should work collectively to check servers and software program
Rule #12: Administration should develop insurance policies and related paperwork to element the extent of knowledge safety and compliance that should be achieved of their enterprise
All this to say—everybody performs a job in staying compliant. Not just for the higher good of the group, however so you possibly can construct and deploy effectively and with confidence that you just’re not going to get 10,000 SOS Slack alerts after your app launches.
As we mentioned, your accountability primarily lies on the software stage. This consists of utilizing protected supply code, making certain correct configurations on your CI/CD pipeline, and extra. It’s possible you’ll be pondering: Okay, however how am I purported to know the way to do this? The excellent news is, you don’t must a safety or compliance whiz, identical to you don’t must be a neurosurgeon to place a Band-Support on a reduce. It’s all about realizing and making use of the correct assets (like a Band-Support as an alternative of taping a serviette over the wound).
To keep away from misconfigurations, you possibly can take a look at the documentation website on your cloud service supplier (CSP). Nonetheless, studying all this data could also be too time consuming. If that’s the case for you, then we propose (moderately extremely suggest) utilizing a safety resolution with automation.
Automate steady compliance with Development Micro Cloud One™ – Conformity
Conformity gives cloud greatest practices to empower cloud builders to innovate within the cloud with confidence. Clients leveraging this service can construct safe and compliant cloud structure and keep away from misconfigurations, comparable to crucial id entry administration (IAM) for a safe and compliant cloud setting.
With Conformity’s real-time cloud service configurations checks are run in opposition to your infrastructure to get a whole view of their safety and compliance baseline and gives actionable intelligence to remediate misconfigurations to start bettering your posture.
Don’t simply take our phrase for it. Attempt it your self with a free 30-day trial.
[ad_2]
