[ad_1]
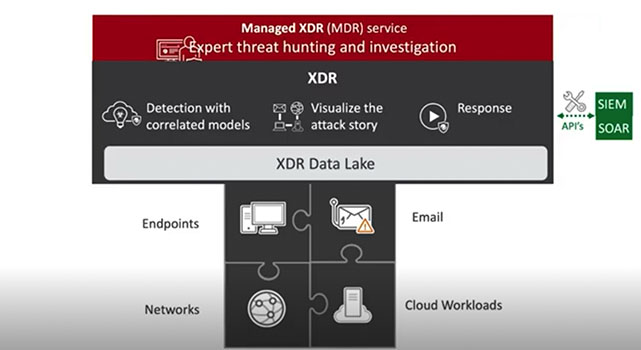
In an ideal world, you require quick detection and response throughout the complete IT atmosphere. But when your SOC is getting information in silos, which is the case for lots of firms, they’ll most likely have to make use of EDR to get detailed visibility for suspicious exercise on endpoints, then a separate siloed view of community safety alerts and site visitors evaluation, and so forth. Every product will find yourself producing its personal perspective of the assault—no correlated data or a consolidated view of the complete chain of occasions. And infrequently, you’ll get differing ranges of element to make it even more durable to attach the dots.
Cue XDR
That is the place prolonged detection and response, or XDR, know-how is available in, linking collectively information from e-mail, servers, endpoints, cloud workloads, and networks to inform the entire story of the assault—as promised. The XDR strategy delivers quicker detection and response throughout the entire atmosphere, because it breaks down the silos and tells the complete story as a substitute of creating the SOC staff dig by means of noisy alerts after which attempt to work out the best way to reply within the many various consoles. XDR will get telemetry from the complete IT atmosphere, utilizing automation and large information to construct the story and save time for the SOC.
In contrast to an API strategy, the place you might be restricted to querying the siloed information units, data might be pooled in a cloud information lake to allow deeper evaluation and generate insights that you could be not have even identified to take a look at. With the correlated detection from XDR know-how, you possibly can robotically filter out the “low-confidence” occasions, behaviors, and actions inside or throughout safety layers, utilizing machine studying, information stacking, and different large information evaluation methods to create a much bigger image and take motion rapidly. As a result of when you possibly can confidently see and shield your total know-how panorama, you possibly can empower your corporation in new, strategic methods.
Mapping to MITRE ATT&CK
Many organizations are beginning to use MITRE ATT&CK to enhance their safety operations by ensuring they’re adequately geared up for frequent adversarial habits. MITRE ATT&CK collects and categorizes frequent assault techniques, methods, and procedures (TTPs), then organizes this data right into a framework. In relation to XDR options, you achieve extra context with mapping to the MITRE ATT&CK framework for quicker detection and better constancy alerts. This framework can be utilized to assist clarify how adversaries behave, what they’re making an attempt to do, and the way they’re making an attempt to do it. Actually, MITRE ATT&CK lately examined in opposition to APT29 with some very attention-grabbing outcomes.
Leverage your individuals
With the predominant expertise hole within the trade, you need the personnel you’ve got to have the ability to work on significant duties. Nevertheless, that may be a bit onerous with the barrage of alerts from single-vector options consuming their day. By robotically correlating risk information from a number of sources, XDR hastens and removes guide steps concerned in investigations and allows safety analysts to rapidly discover the complete story of an assault. Eradicating the low-confidence occasions and repetitive duties frees them to have the ability to work on the dear tasks which might be required to safe the group and depart you with peace of thoughts.
Hear extra on the actual frontier for 2021 in XDR.
Casey, T. (2018, Might 28). Survey: 27 P.c of IT professionals obtain greater than 1 million safety alerts every day: Imperva. Retrieved from https://www.imperva.com/weblog/27-percent-of-it-professionals-receive-more-than-1-million-security-alerts-daily/
Oltsik, J. and Clark, J, (2020, August). Safety Infrastructure and Market Modifications in Progress, Enterprise Technique Group
[ad_2]
