[ad_1]

A phishing operation has reduce and pasted parts of at the very least 5 different phishing kits to create its personal assault platform, sending out password-reset and fax-and-scanner notifications in vital campaigns earlier this 12 months, in keeping with researchers with the Microsoft 365 Defender Menace Intelligence Workforce.
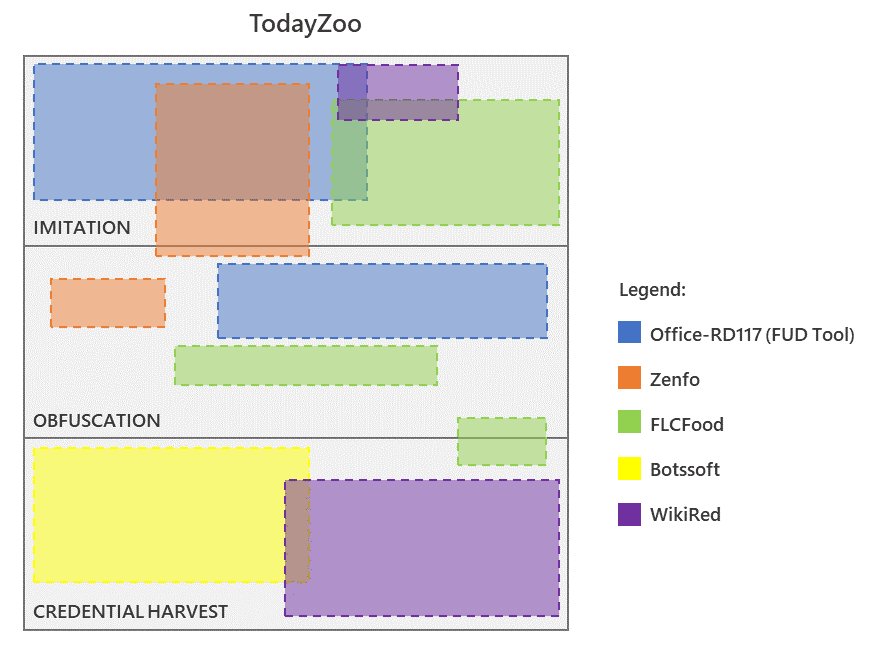
The TodayZoo equipment, as Microsoft dubbed the framework, seems to extensively use code from one other equipment, generally known as DanceVida, whereas different parts considerably match the code from at the very least 5 different phishing kits. Microsoft first found the phishing equipment in December 2020, however a sequence of main campaigns in March and June 2021 tried to steal credentials from Microsoft customers, main the corporate’s risk intelligence crew to research the equipment.
Calling the cybercriminal device a “Franken-phish” due to its use of elements from different phishing kits, the equipment appears to carry collectively totally different parts of different phishing instruments quite than use a phishing-as-a-service providing, says Tanmay Ganacharya, accomplice director for safety analysis at Microsoft Defender.
“In the end, phishing kits — just like malware — are more and more modular and typically defy clear household attribution consequently,” he says. “Different kits which might be related and have shared code are additionally well-protected at the moment, however we see new kits and phish pages each day that defy normal naming as they morph so shortly.”
Phishing continues to be an especially in style means of harvesting delicate info and bonafide credentials from unwary customers. Profitable assaults are much less more likely to come via an e-mail consumer and extra more likely to goal cellular customers, in keeping with a report launched this week by Jamf, a supplier of enterprise administration instruments for Apple computer systems and units. Round 10% of customers on cellular units have clicked on a phishing hyperlink up to now 12 months, a rise of 160% over the previous 12 months, the corporate states in its “Phishing Traits Report 2021.”
The preferred manufacturers focused by phishing assaults in 2021 included Apple, PayPal, Amazon, and Microsoft, the report states.
“Phishing assault supply has developed far past poorly-worded emails providing ‘unclaimed lottery winnings,'” the Jamf report states. “They don’t seem to be solely extra customized and extra convincing, they’re reaching customers in additional locations than ever earlier than and more and more going past customers to focus on enterprise credentials and knowledge.”
Phishing Kits Up ClosePhishing kits usually have three main parts: an imitation functionality that creates login pages that match carefully to a focused model; a set of options that obfuscate the malicious code within the pages, which additionally consists of anti-analysis options; and code that harvests credentials, or different delicate info, from the person and sends it again to the attacker.
In its evaluation, Microsoft discovered TodayZoo and DanceVida had a couple of 30% to 35% overlap between the code included within the two kits. The 2 codebases diverged considerably in how they dealt with credential harvesting.
“[B]ecause of the consistency within the redirection patterns, domains, and different methods, techniques, and procedures (TTPs) of its associated campaigns, we consider that the actors behind it got here throughout an previous phishing equipment template and changed the credential harvesting half with its personal exfiltration logic to make TodayZoo solely for his or her nefarious functions,” in keeping with the Microsoft researchers.
The TodayZoo campaigns all used the identical four-step assault, sending e-mail to focused customers who then could be redirected to an preliminary web page. Then victims’ browsers had been redirected to a second web page, which then despatched the sufferer to a last touchdown web page hosted by — in virtually each case — service supplier Digital Ocean.
“[T]his analysis additional proves that the majority phishing kits noticed or accessible as we speak are primarily based on a smaller cluster of bigger equipment ‘households,'” the Microsoft evaluation states. “Whereas this pattern has been noticed beforehand, it continues to be the norm, given how phishing kits we’ve seen share massive quantities of code amongst themselves.”
The code for TodayZoo, and the scripts used to create its pages, had a lot of artifacts left over from the unique supply of the code, in keeping with Microsoft. Such lifeless hyperlinks and callbacks to different kits could point out that many phishing equipment distributors and phishing operators are shortly grabbing items of code from accessible sources to construct their instruments, Microsoft says.
“We are going to seemingly see extra cobbled-kits sooner or later, in addition to simpler kits generally as among the extra generic [and] apparent ones fall out of use in favor of extra evasive kits that bypass sandbox evasion, incorporate CAPTCHAs, encode supply, or use separate programming languages or useful resource sorts,” says Phillip Misner, principal safety group supervisor at Microsoft.
Misner warned that credential phishing will proceed to be a hazard to companies, particularly if firms don’t adequately filter out suspicious e-mail messages and senders. Companies ought to take into account adopting multifactor authentication and harden the configurations for his or her mail servers to make phishing assaults tougher, he says.
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.