[ad_1]

The identical customary that permits wi-fi gadgets to stay linked and roam between entry factors additionally permits attackers to simply gather crucial Wi-Fi keys that may then later be hashed to seek out Wi-F community passwords, a researcher present in a wardriving experiment.
Ido Hoorvitch, a safety researcher with id and entry administration supplier CyberArk, discovered that he might get well the community passwords for greater than 70% of the networks he scanned, merely by utilizing info collected as he pedaled his bike—and typically walked or drove—alongside the streets in Tel Aviv, Israel.
He used a selfmade wi-fi scanner primarily based on a $50 community card linked to a laptop computer operating Ubuntu Linux, and the Hcxdumptool device out there on GitHub to gather WiFi Protected Entry (WPA) packets from close by networks.
Many wi-fi networks in Israel use a cellphone quantity as a password. Utilizing a customized decryption system comprising of eight graphic processing models (GPUs), Hoorvitch might check every doable password in about 15 seconds.
“All of us know that passwords are problematic—they’re too laborious to recollect. And if they’re simple to recollect, then they’re too simple to crack,” Hoorvitch says. “What’s particular about this analysis is that it modified the state from a speculation to an empirical experiment. We now know that the WiFi password for many of the networks is actually not safe sufficient.”
Wi-fi networks proceed to be a weak level for a lot of customers and enterprises. In Might 2021, a doctoral researcher at New York College Abu Dhabi warned that each Wi-Fi system is susceptible to no less than one in every of three design flaws, after spending 9 months serving to main wireless-device producers shut the vulnerabilities. In 2017, the identical researcher warned {that a} collection of points might enable attackers to conduct key reinstallation assaults (KRACKs), which might enable them to hijack wi-fi connections.
Cybersecurity specialists have additionally warned that weak, default, or simply guessable passwords put wi-fi networks in danger. With extra workers working from dwelling, shopper Wi-Fi networks have additionally grow to be a gateway to company knowledge.
“The specter of a compromised WiFi community presents severe danger to people, small enterprise homeowners and enterprises alike,” the CyberArk weblog publish acknowledged. “And as we’ve proven, when an attacker can crack greater than 70% of WiFi networks in a significant international metropolis with relative ease, higher consideration should be paid to defending oneself.”
Within the newest analysis, CyberArk researchers confirmed that an attacker—fairly then needing to be close by a focused wi-fi community—might file the required packets as they drove via a neighborhood after which use that info to have a excessive likelihood of discovering the password to any specific community.
The Drawback with PMK
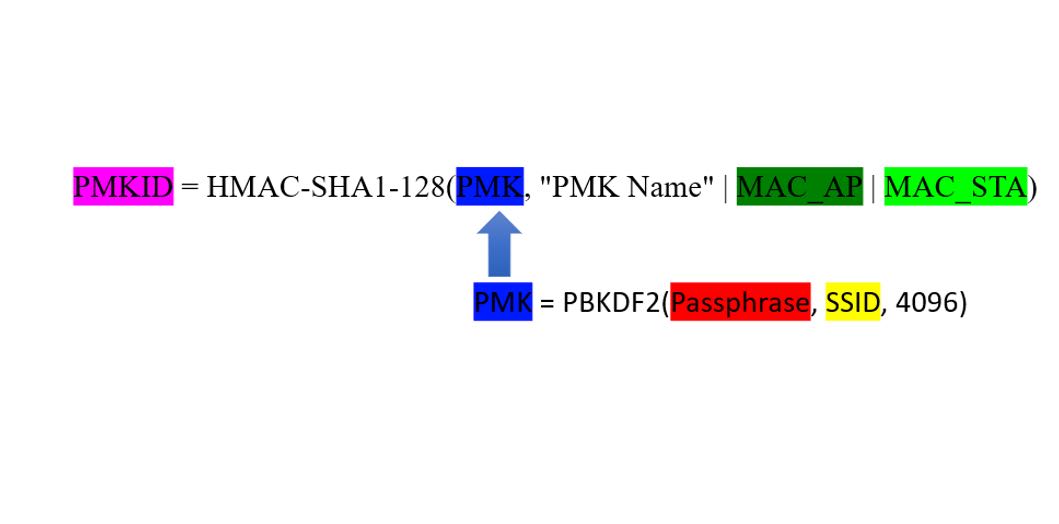
The important thing to the assault is poor password choice and the flexibility of attackers to seize the Pairwise Grasp Key (PMK) Identifier (PMKID) and different crucial info. The PMK permits a tool to stay linked to a community even when the system strikes to a distinct entry level on the identical community. Fairly than requiring the consumer to re-authenticate, the system retains the PMK to ship as its authentication. Most shopper networks don’t use this performance, however typically the function is on by default.
The assault methodology, found by Jens Steube, the lead developer for Hashcat, offers attackers the flexibility to scan networks and uncover passwords at at a later time.
The assault makes use of 4 piece of information from the community: The wi-fi community SSID, the {hardware}—or media entry management (MAC)—handle of the entry level, the MAC handle of the consumer laptop, and the PMKID that the pc and entry level use to stay authenticated. By combining data of a wi-fi networks SSID, the attacker can create a listing of PMKs for doable passwords. These PMKs are then utilized in one other hashing algorithm to create a listing of PMKIDs. An attacker simply has to maintain altering the password to create new PMKs, which is then used to create new PMKIDs, till a match is discovered.
The variety of potential alphanumeric-plus-symbols mixtures creates a large search area, however Hoorvitch and CyberArk used the truth that many Israeli customers use their mobile phone numbers as their password as a approach to restrict the search. For every community, the researcher needed to strive each risk for 8-digit cell numbers or 100 million. Whereas that appears to be a large endeavor, the worst case state of affairs—having to strive each doable quantity—requires 15 seconds on CyberArk’s customized eight-GPU decryption machine or about 9 minutes on a superb laptop computer, Hoorvitch says.
Of the 5,000 networks on which the researcher collected info, 44% had a mobile phone quantity as a password, whereas one other 18% had been discovered on the widespread password listing generally known as RockYou.txt. The remaining had been different easy mixtures of numbers and letters.
In whole, the researchers discovered passwords for 3,633 of the 5,000 focused networks, and certain a few of the relaxation might have been discovered as properly.
“We all know we will crack more durable passwords, however that’s not the concept of this analysis,” he says. “What bothered me is just not, [whether] somebody didn’t have a posh password, however whether or not, with three- to 4 days on a standard laptop computer, what can we crack?”
Selecting a non-guessable, complicated password for wi-fi community ought to defend in opposition to the assault. Whereas 18% of passwords had been discovered through the use of the favored password listing, RockYou.txt, virtually half of the overall used solely numbers, and most of these the customers’ mobile phone quantity, a scheme that gives little safety.
Whereas multi-factor authentication (MFA) is usually the answer to password safety points and would additionally strengthen a wi-fi community’s safety, MFA is notoriously laborious to implement on shopper WiFi networks.
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.