[ad_1]

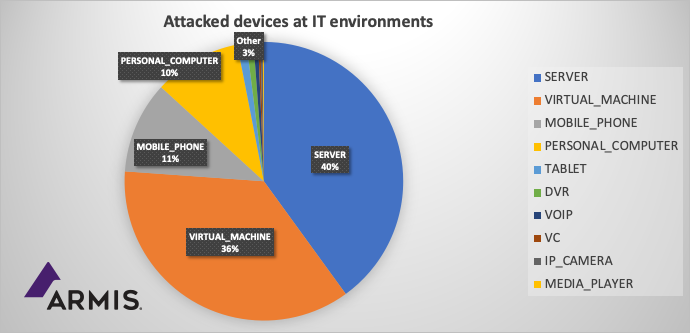
Safety groups working to mitigate their organizations’ publicity to the Log4j vulnerability have loads of challenges to beat. They embody scoping the total extent of publicity, determining workarounds for techniques that can not be patched, and making certain third-party services and products have been secured.For a lot of, the duty can be additional sophisticated by the necessity to consistently monitor for indicators of attackers trying to use the flaw or indications they may have already got been compromised, safety consultants stated this week. Log4j is a logging instrument that’s current in almost all Java functions. A crucial distant code execution vulnerability (CVE-2021-44228) exists in variations of Log4j from 2.0-beta9 to 2.14.1 that permits attackers to take full management of susceptible techniques. The Apache Basis launched an up to date model of the instrument (Apache Log4j 2.15.0) final week, then issued a second replace on Tuesday as a result of the unique repair didn’t absolutely shield towards denial-of-service (DoS) assaults and knowledge theft.The flaw is extensively thought-about to be among the many most harmful in latest reminiscence as a result of it’s straightforward to use and is current throughout nearly each IT atmosphere. Veracode, as an example, discovered 88% of its clients use some model of Log4j and 58% have a susceptible model of their environments.Attackers world wide have been trying to use the flaw from the second it was first disclosed final week. Quite a few distributors have noticed makes an attempt to distribute coin miners, ransomware, distant entry Trojans, Internet shells, and botnet malware. Armis on Wednesday reported some 35% of its clients had been underneath energetic assault through the vulnerability and 31% had a Log4j-related risk on unmanaged gadgets. The safety vendor stated it had noticed as many as 30,000 tried exploits towards its clients. A number of different distributors have reported comparable exercise.Armis discovered essentially the most focused property in IT environments up to now have been servers, digital machines, and cell gadgets. In OT networks, 49% of compromised gadgets have been digital machines and 43% have been servers. Different focused gadgets in OT networks embody IP cameras, human machine interface (HMI) gadgets, and SCADA techniques.Scoping the ProblemOne main problem organizations face in defending towards assaults focusing on Log4j is determining their full publicity to the risk, in keeping with safety consultants. The vulnerability may be current not simply on a company’s Web-facing property, however on inner and back-end techniques, community switches, SIEM and different logging techniques, internally developed and third-party apps, in SaaS and cloud providers, and environments they won’t even learn about. The interdependencies between completely different functions and elements imply even when a part doesn’t instantly have the vulnerability, it may well nonetheless be affected by it.The way in which Java packing works can typically make it arduous to establish affected functions, Noname Safety says. For instance, a Java archive (JAR) file may comprise all of the dependencies — together with the Log4j library — of a specific part. However that JAR file may comprise one other JAR file that, in flip, may comprise one more JAR file — basically burying the vulnerability a number of layers deep, the safety vendor stated. “One of many important challenges that organizations face in mitigating the vulnerabilities present in Log4j is figuring out all compromised property,” says Gustavo Palazolo, risk analysis engineer at Netskope. The Log4j Apache Java-based logging library may be very common and can be utilized by many functions, in addition to by IoT gadgets and legacy techniques which might be maintained for backwards compatibility, he provides. Even when an software is discovered to be susceptible, updating it may be troublesome as a result of a company might not have the ability to afford the downtime or lack correct patch administration controls. “Due to this fact, the time between figuring out all compromised techniques and fixing the issue can take a very long time in some eventualities,” Palazolo says.APIs and Third-Social gathering RisksApps will not be the one concern. The Log4j vulnerability can have an effect on software programming interface (API) environments as properly. API servers that comprise the vulnerability supply a horny assault vector as a result of many organizations have restricted visibility over their API stock and their APIs’ habits, Noname stated. A enterprise that does not use the Log4j logging framework may be utilizing trusted third-party APIs that comprise the Log4j flaw, thereby exposing it to threat.”For a company to attenuate the danger of [Log4j vulnerability] exploitation through APIs, a number of steps should be taken,” says Aner Morag, vice chairman of expertise at Noname Safety. These embody mapping all servers which might be serving APIs with any Java service, not permitting any person enter to succeed in a log message on any API server, utilizing a proxy or different mechanism to manage which servers back-end providers can connect with, and placing APIs behind an API gateway or load balancer, Morag says.One other problem organizations face is making certain all third-party services and products they use are correctly patched or have mitigations towards the flaw. “Lots of vendor merchandise are affected, [and] the checklist of affected distributors is rising on an on a regular basis foundation,” says Tom Gorup, vice chairman of safety operations at Alert Logic. “Not all distributors might have patches out there.”Gorup recommends safety groups test their distributors’ web sites or attain out to them instantly to grasp if any of their merchandise are affected. A vendor may be susceptible however have launched mitigation steps to guard its clients. “At minimal, you’ll need to perceive how one can validate your property have acquired the replace,” Gorup notes. He additionally suggests safety groups test lists of susceptible merchandise which have grow to be out there over the previous few days, akin to this one at GitHub.”A response to this vulnerability may very well be, ‘We don’t use Java,'” Gorup says. “The place this may be true, your third-party software program may need it embedded, which can end in your vulnerability scans not exhibiting up [the threat].”
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.