[ad_1]

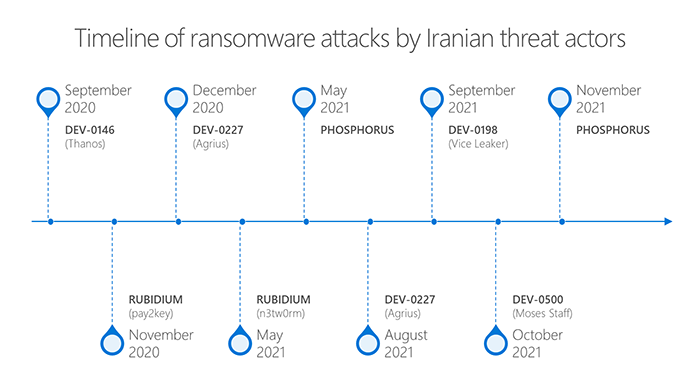
Cybersecurity companies in america, the UK, and Australia warned on Wednesday that Iran-linked cyberattack teams had been ramping up operations, concentrating on vulnerabilities in enterprise know-how to compromise organizations within the US and Australia.In a joint advisory issued Nov. 17, the FBI, Cybersecurity and Infrastructure Safety Company (CISA), Australian Cyber Safety Centre (ACSC), and the UK’s Nationwide Cyber Safety Centre (NCSC) blamed Iran for a broad rise in assaults utilizing vulnerabilities in Fortinet’s FortiOS and Microsoft Change. The attackers typically activate BitLocker on compromised Home windows machines to encrypt knowledge for ransom or hinder operations, the companies mentioned.Three Fortinet vulnerabilities have been used since at the very least March in opposition to US targets, whereas each the US and Australia have seen assaults concentrating on the Microsoft Change ProxyShell situation, the advisory acknowledged.”The Iranian government-sponsored APT actors are actively concentrating on a broad vary of victims throughout a number of U.S. crucial infrastructure sectors, together with the Transportation Sector and the Healthcare and Public Well being Sector, in addition to Australian organizations,” acknowledged CISA and the FBI in a joint advisory, including that the assaults appear extra targeted on gaining benefit earlier than organizations patch particular flaws, moderately than particularly concentrating on crucial infrastructure. “These Iranian government-sponsored APT actors can leverage this entry for follow-on operations, resembling knowledge exfiltration or encryption, ransomware, and extortion.”These notices come lower than three weeks after a high Iranian official blamed the US and Israel for assaults disrupting gasoline gross sales in Iran. In late October, Iran’s civil protection chief, Gholamreza Jalali, blamed “the Zionist Regime, the Individuals and their brokers” for the outage, which affected 1000’s of gasoline stations, in accordance with a Reuters report.FBI officers additionally reportedly despatched out a non-public trade notification (PIN) warning corporations that Iranian attackers try to purchase stolen knowledge concerning e mail messages and community data on underground boards. In addition they warned corporations which have had knowledge stolen to be careful for future assaults.The cyber battle demonstrates why personal trade and authorities must work collectively, mentioned Mike Wiacek, CEO and co-founder at security-monitoring agency Stairwell, in a press release despatched to Darkish Studying.”No single get together, whether or not it’s a firm or a rustic, can clear up issues of this magnitude on their very own,” he mentioned. “The power to recursively determine threats whether or not previous, current or future, and creating defenses which might be imperceptible to attackers are required. Fragmented viewpoints solely profit unhealthy actors, so working collectively and sharing data and intelligence is totally crucial.”Iran has dramatically elevated its on-line capabilities because the US and Israel reportedly sabotaged the nation’s nuclear program utilizing the Stuxnet worm in 2009. The US, Israel, and Saudi Arabia are widespread targets of Iran.In an evaluation of Iran-linked teams revealed Nov. 16, Microsoft described eight completely different cyber operations teams both primarily based in or working within the pursuits of Iran. Microsoft’s naming schemes point out the teams are Phosphorus, Rubidium, Curium, and 5 further teams that designate creating clusters of exercise that Microsoft has not but named.Microsoft’s Risk Intelligence Middle famous a couple of tendencies within the teams’ operations. Iranian-backed teams are more and more utilizing ransomware, wipers, and different threats to disrupt targets, with six recognized teams deploying ransomware throughout an assault, the corporate famous. The teams are additionally turning into extra affected person and protracted of their operations, particularly in social engineering campaigns, however nonetheless use credential spraying and different brute-force assaults on their targets, Microsoft acknowledged.”As Iranian operators have tailored each their strategic objectives and tradecraft, over time they’ve developed into extra competent risk actors able to conducting a full spectrum of operations together with data operations, disruption and destruction, [and] assist to bodily operations,” Microsoft acknowledged in its evaluation.The extent of cyber operations between Iran and the US has elevated as Iran has invested in additional cyber capabilities and the US has allowed extra aggressive actions as a part of its Defend Ahead coverage. Iranian teams have been blamed for assaults together with ransomware, disk wipers, cellular malware, phishing assaults, password spraying, the usage of mass exploits, and assaults concentrating on provide chains.But the rise in tensions will possible not deter Iran and will trigger its personal points. Russian risk actors, for instance, have taken over Iranian infrastructure so assaults would seemingly be coming from Iran. In the meantime, hacktivists have taken credit score for lots of the assaults for which Iran blames its rivals.
[ad_2]
Sign in
Welcome! Log into your account
Forgot your password? Get help
Privacy Policy
Password recovery
Recover your password
A password will be e-mailed to you.